What is and how to generate a HASH ?
Transforming a large amount of data into a small amount of information.
A cryptographic scatter function or cryptographic hash function is a hash function considered almost impossible to reverse, that is, to recreate the input value using only the scatter value. These unidirectional hash functions have been called “the workers of modern cryptography”.
The input data is usually called message, and the message scatter value summarized or simply summary.
The hashes are also called:
- hash function, or:
- checksums;
- hash codes;
- and among other nomenclatures.
Broadly speaking:
A hash is a sequence of bits generated by an algorithm, generally represented in hexadecimal base, that allows the visualization in letters and numbers (0 to 9 and A to F). Or simply: “hash is the transformation of a large amount of data into a small amount of information”.
There are types of hashes (or hash functions), they can be: md5, sha256, whirpool and among others less used. For more information watch the video below and see the links at the end of this post.
Watch The Video
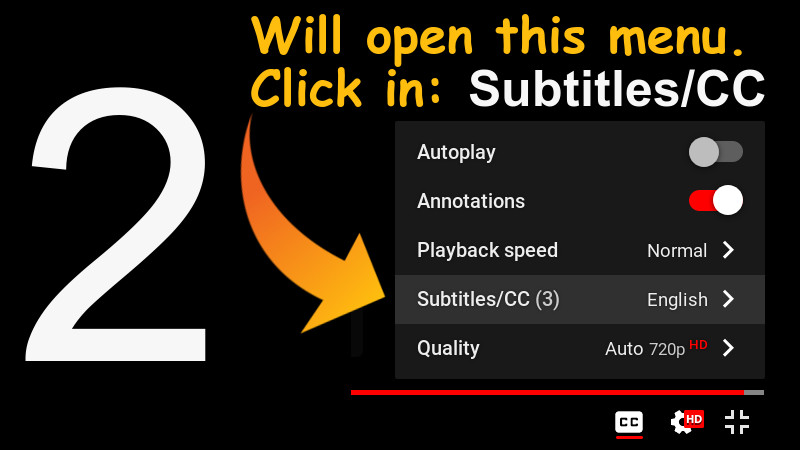
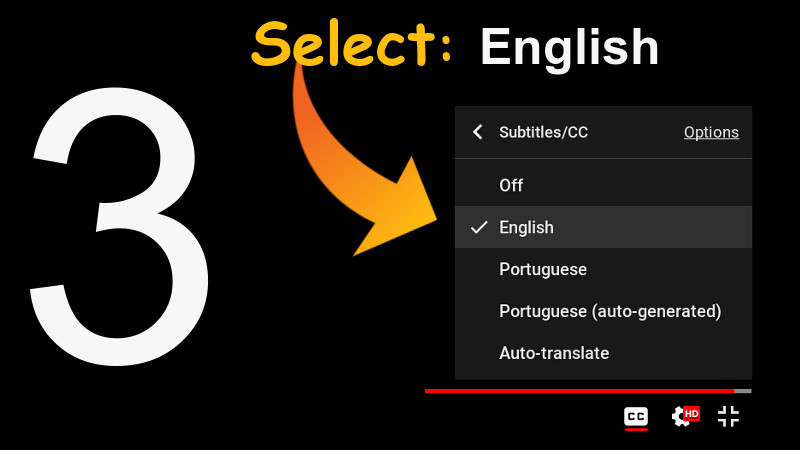
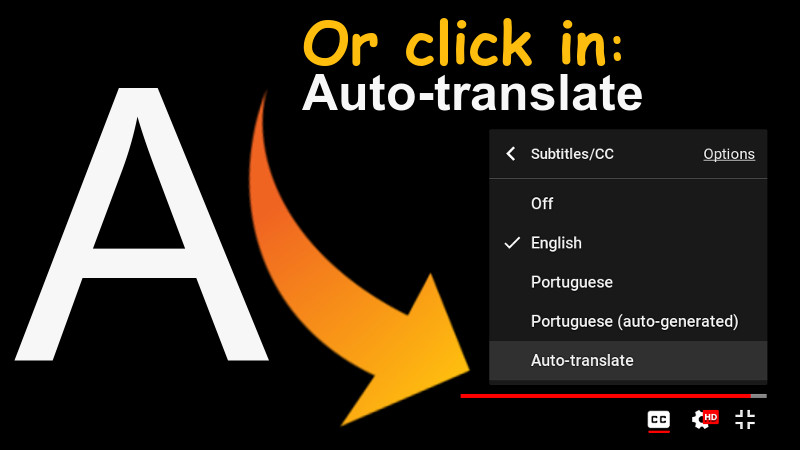
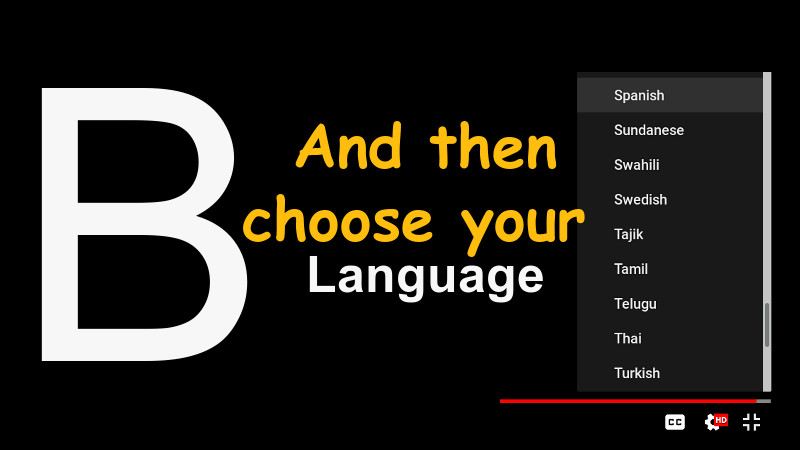
The video has English subtitles native to the video itself and with the correct translation. To enable, use the settings in the footer of the video itself, according to the images shown here below.
CLICK ON IMAGES TO VIEW INTO LARGER RESOLUTION.
Tutorial for subtitles in Youtube

Comments